Synaptic Web says...

Off-Page SEO: A Guide For Beginners
- Written by: Matthew Woodward
- Category: Blog
- Hits: 5097
Most people have a good idea of what they need to do with on-page SEO but get slightly lost when it comes to off-page SEO. This little guide is going to rectify that!
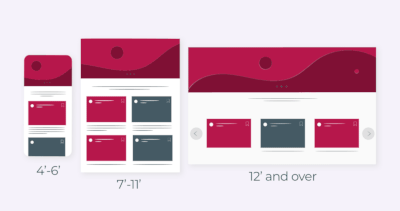
Mobile-First, Adaptive and Responsive Designs: how do they differ?
- Written by: Vitaly Kuprenko
- Category: Blog
- Hits: 6343
What is the best method for creating a design for a website? Today, most experts think it’s better to build a complete mobile interface first and then adapt it for desktops.
Read more: Mobile-First, Adaptive and Responsive Designs: how do they differ?

The SEO Checklist You Will Need In 2021
- Written by: Chain Reaction
- Category: Blog
- Hits: 4140
SEO continues to grow and grow, and 2021 looks set to be one of the most significant years yet for the marketing technique. What do I need to know? That's a fair question, so let's get stuck into some thoughts straight away.

